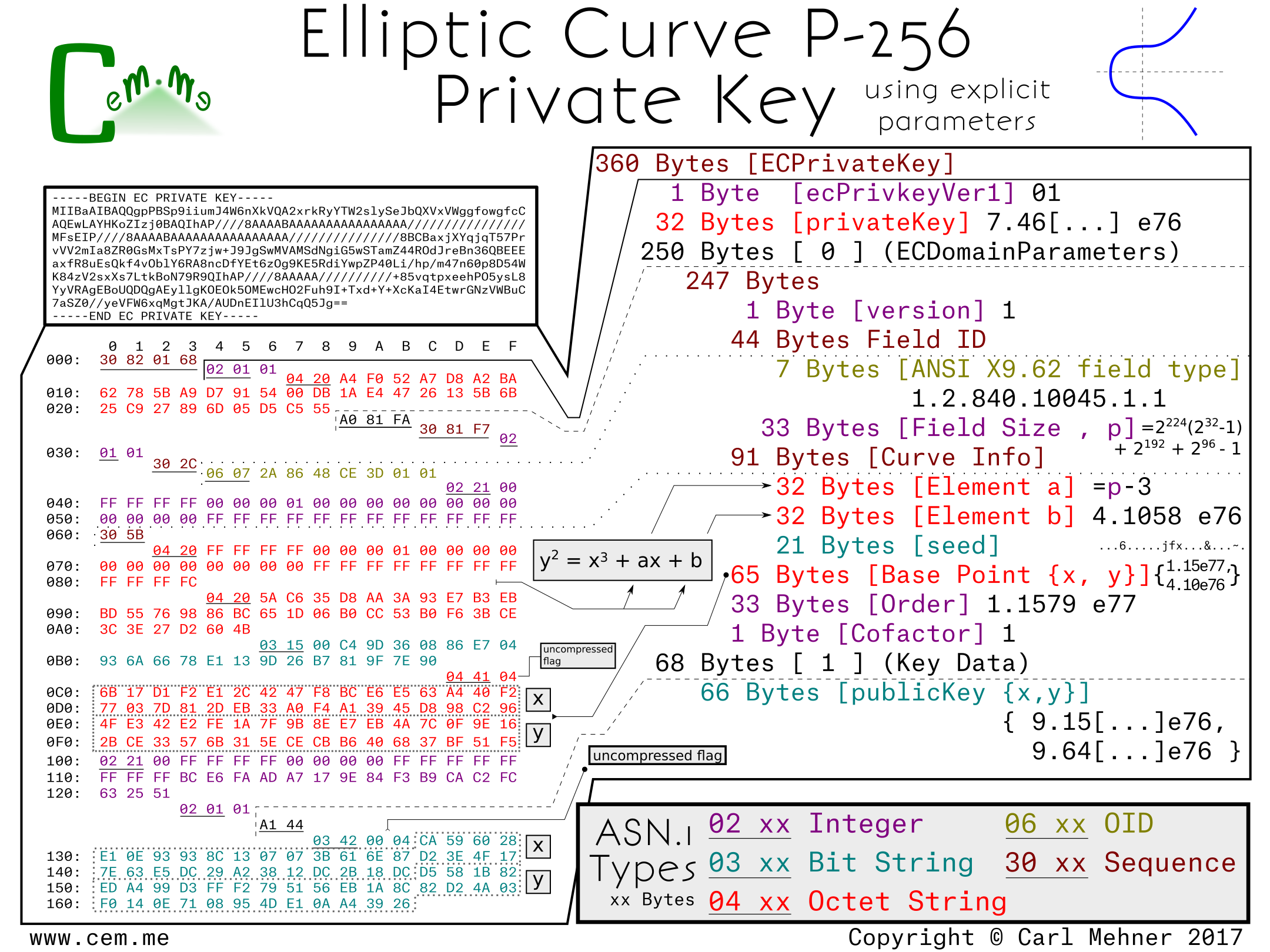
![PDF] Fast Implementation of NIST P-256 Elliptic Curve Cryptography on 8-Bit AVR Processor | Semantic Scholar PDF] Fast Implementation of NIST P-256 Elliptic Curve Cryptography on 8-Bit AVR Processor | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/adde810e267c2c20cb9131b7e48387ef8bc2c807/8-Figure1-1.png)
PDF] Fast Implementation of NIST P-256 Elliptic Curve Cryptography on 8-Bit AVR Processor | Semantic Scholar
![PDF] Fast Implementation of NIST P-256 Elliptic Curve Cryptography on 8-Bit AVR Processor | Semantic Scholar PDF] Fast Implementation of NIST P-256 Elliptic Curve Cryptography on 8-Bit AVR Processor | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/adde810e267c2c20cb9131b7e48387ef8bc2c807/11-Table1-1.png)
PDF] Fast Implementation of NIST P-256 Elliptic Curve Cryptography on 8-Bit AVR Processor | Semantic Scholar

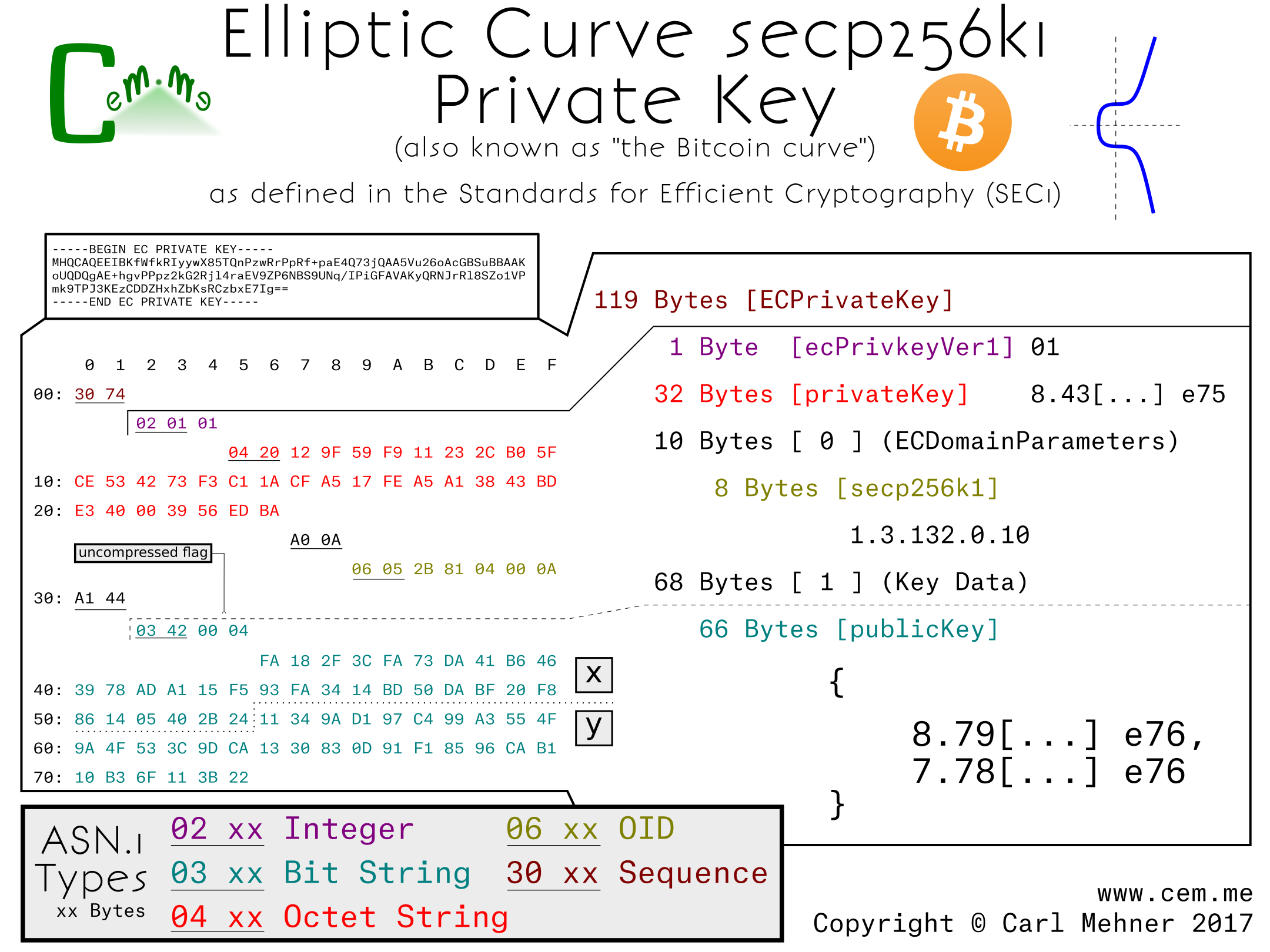
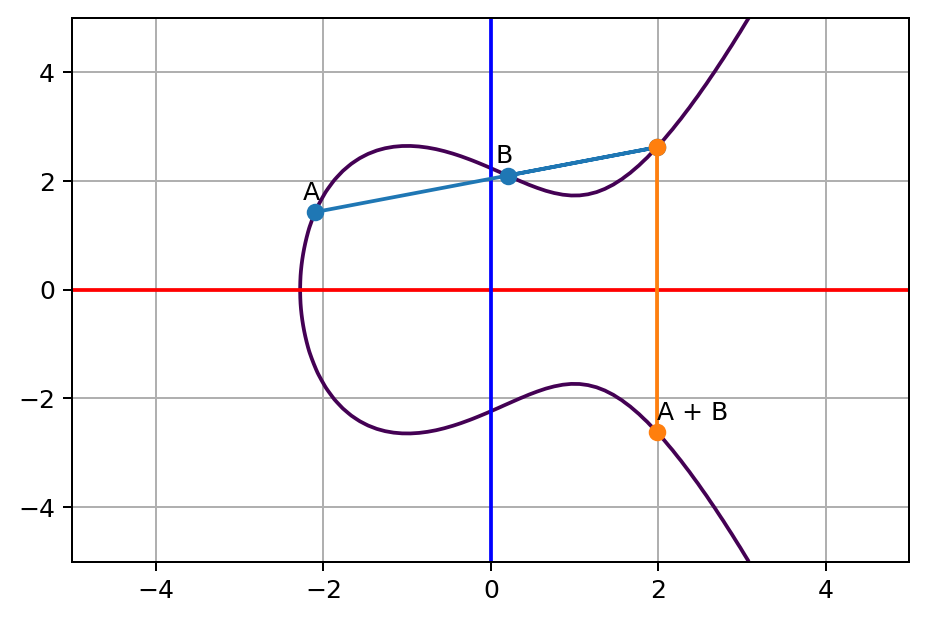
Everyone Loves Curves! But Which Elliptic Curve is the Most Popular? - Malware News - Malware Analysis, News and Indicators
![PDF] Fast Implementation of NIST P-256 Elliptic Curve Cryptography on 8-Bit AVR Processor | Semantic Scholar PDF] Fast Implementation of NIST P-256 Elliptic Curve Cryptography on 8-Bit AVR Processor | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/adde810e267c2c20cb9131b7e48387ef8bc2c807/13-Table3-1.png)
PDF] Fast Implementation of NIST P-256 Elliptic Curve Cryptography on 8-Bit AVR Processor | Semantic Scholar

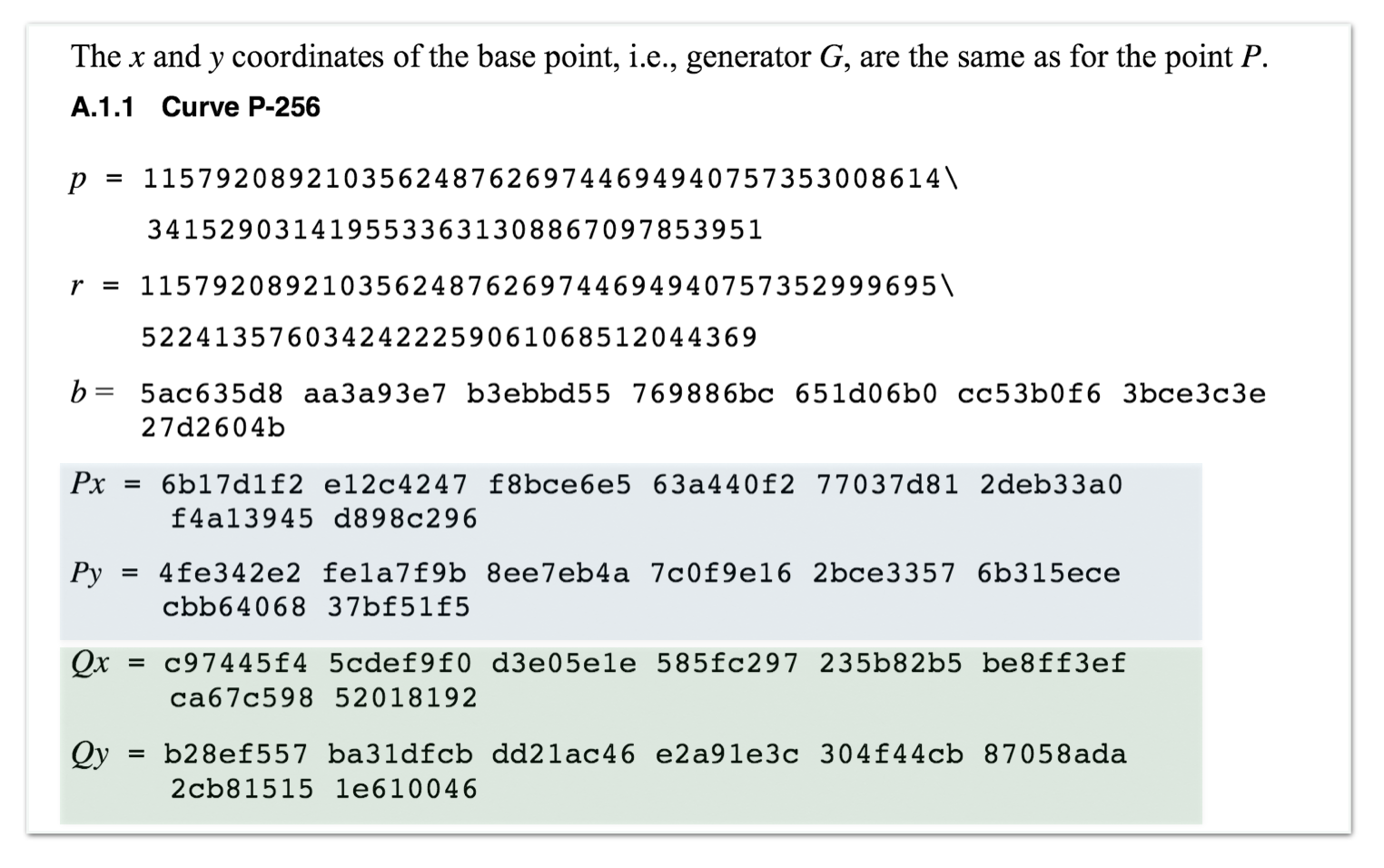
EW_{256357}$$ : A New Secure NIST P-256 Compatible Elliptic Curve for VoIP Applications' Security | SpringerLink
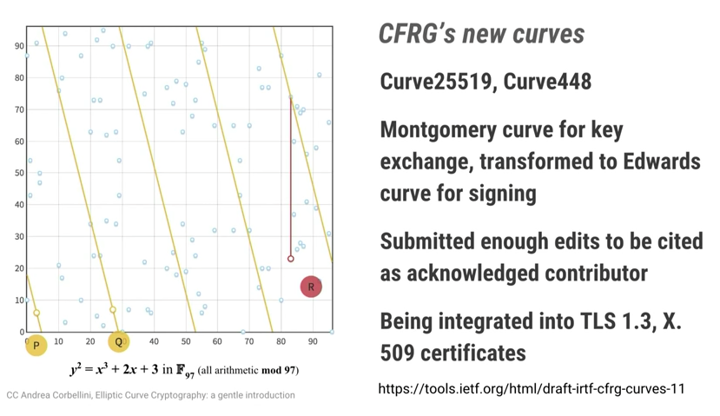
Everyone Loves Curves! But Which Elliptic Curve is the Most Popular? - Malware News - Malware Analysis, News and Indicators

Everyone Loves Curves! But Which Elliptic Curve is the Most Popular? - Malware News - Malware Analysis, News and Indicators