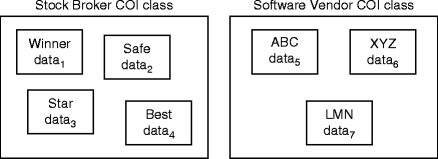
Week 8 - Friday. What did we talk about last time? Bell-La Padula model Clark-Wilson model Chinese Wall model Biba model. - ppt download

Week 8 - Friday. What did we talk about last time? Bell-La Padula model Clark-Wilson model Chinese Wall model Biba model. - ppt download





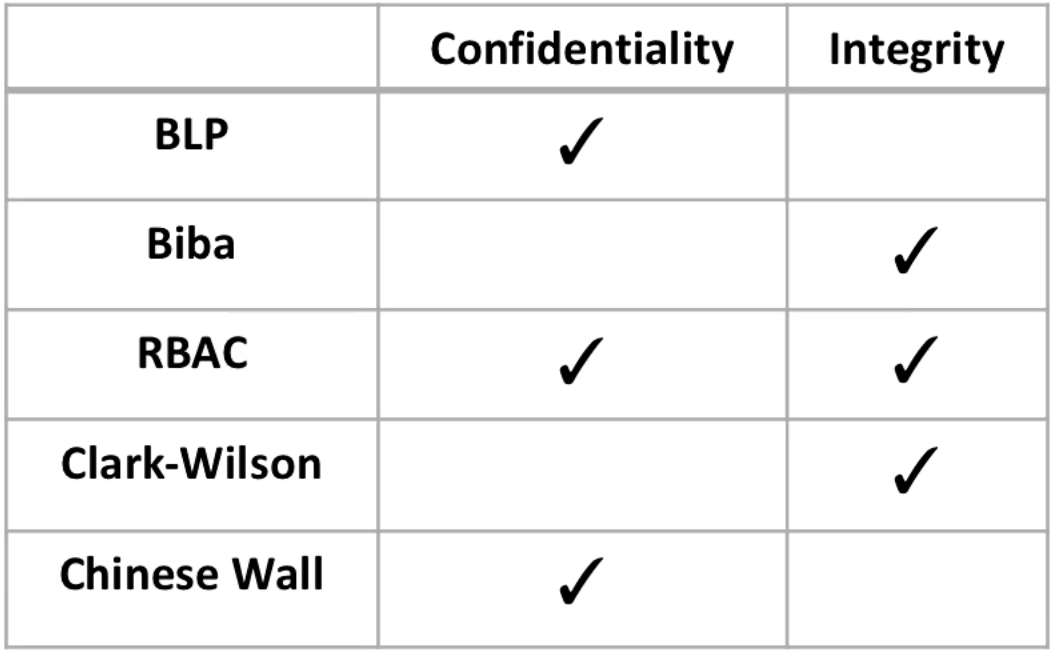
![PDF] Study of Access Control Models | Semantic Scholar PDF] Study of Access Control Models | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7c6c6a84d6c05dfdf337296cdb9953131fa8122d/4-TableII-1.png)





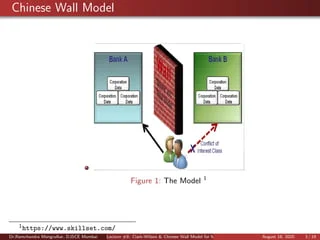


![PDF] A new Access Control model based on the Chinese Wall Security Policy Model | Semantic Scholar PDF] A new Access Control model based on the Chinese Wall Security Policy Model | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/97ee8acea2981bff76667b95eb65514c6bdd8fc3/4-Figure2-1.png)