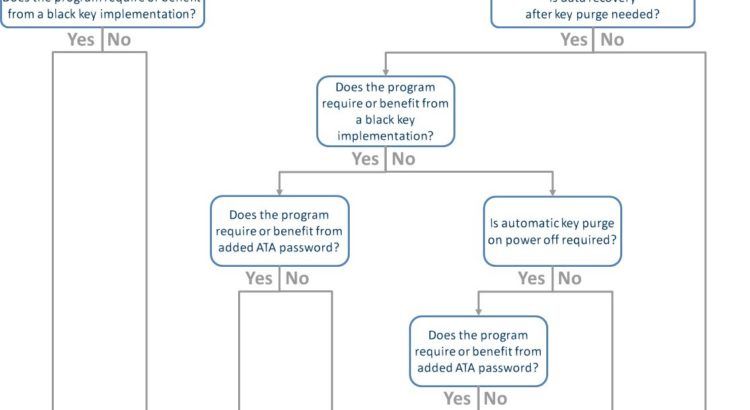
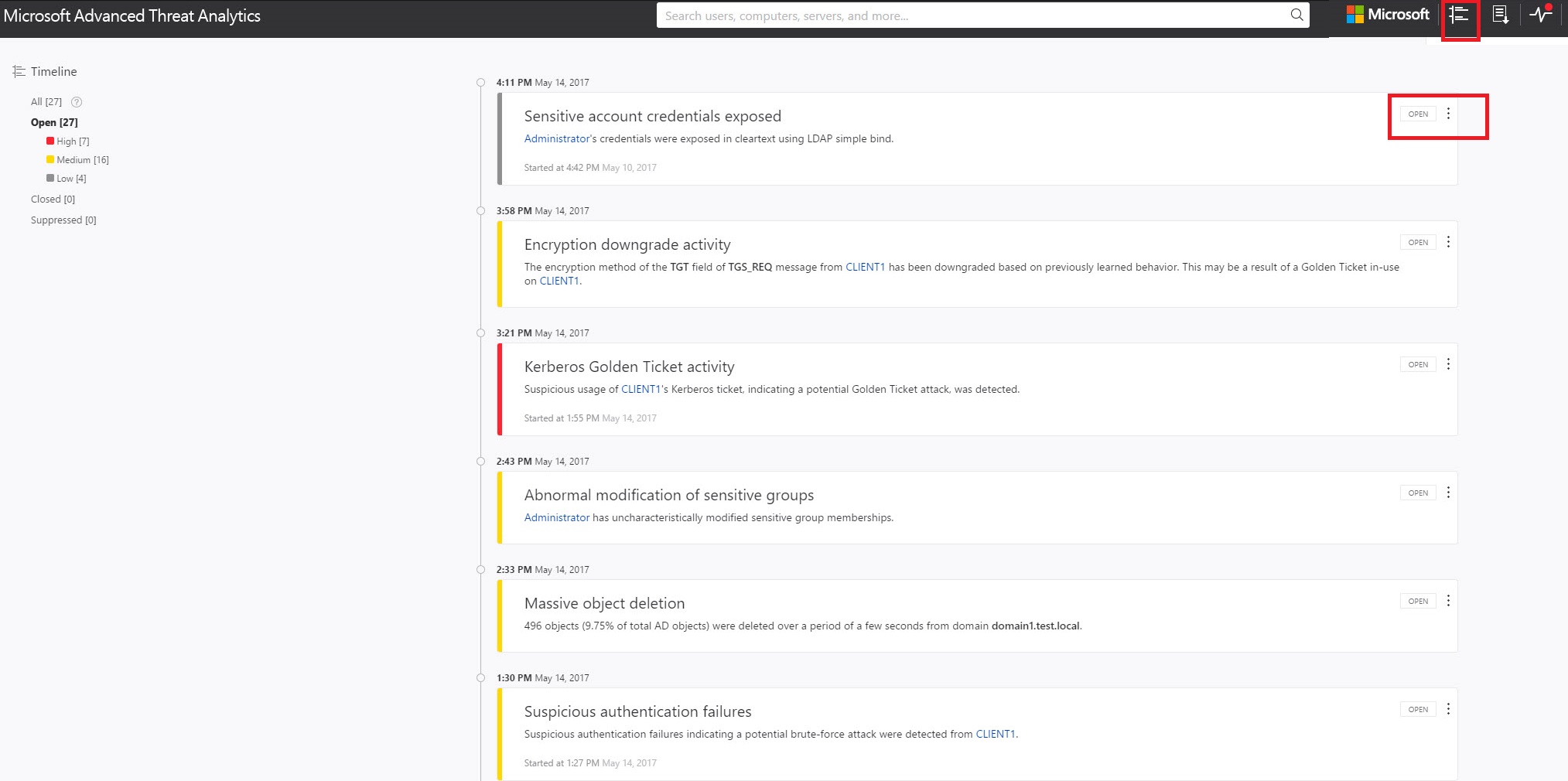
Lab of a Penetration Tester: Week of Evading Microsoft ATA - Day 2 - Overpass-the-hash and Golden Ticket
![Cisco ATA 191 and ATA 192 Analog Telephone Adapter Provisioning Guide for Multiplatform Firmware - Deployment and Provisioning [Cisco ATA 190 Series Analog Telephone Adapters] - Cisco Cisco ATA 191 and ATA 192 Analog Telephone Adapter Provisioning Guide for Multiplatform Firmware - Deployment and Provisioning [Cisco ATA 190 Series Analog Telephone Adapters] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/390001-400000/393001-394000/393514.eps/_jcr_content/renditions/393514.jpg)
Cisco ATA 191 and ATA 192 Analog Telephone Adapter Provisioning Guide for Multiplatform Firmware - Deployment and Provisioning [Cisco ATA 190 Series Analog Telephone Adapters] - Cisco
We've introduced 2 new features since our blog on rotating #passwordstate Encryption Keys . You can now set reminders to rotate them and change the encryption between AES 256 Bit and FIPS

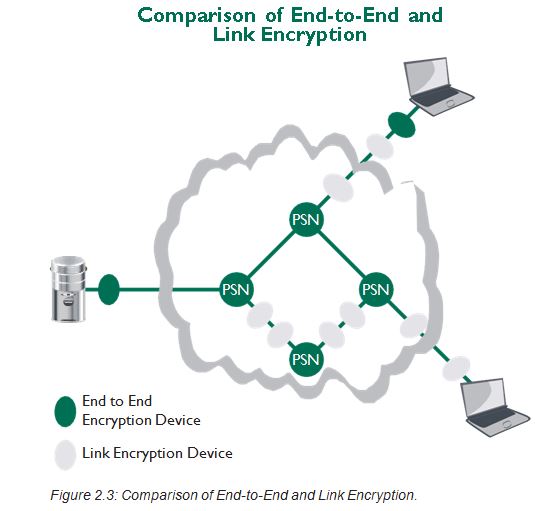
The frame work of the portable hard disk encryption/decryption system... | Download Scientific Diagram
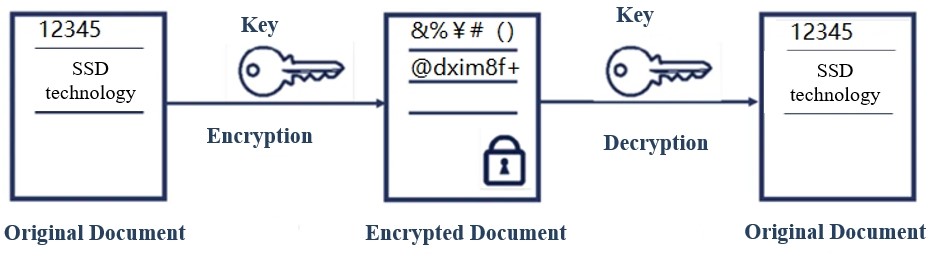
![PDF] Self-Encrypting Disks pose Self-Decrypting Risks How to break Hardware-based Full Disk Encryption | Semantic Scholar PDF] Self-Encrypting Disks pose Self-Decrypting Risks How to break Hardware-based Full Disk Encryption | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f26acc62a873c071651d721167fc2942cbb9a3c4/8-Figure2-1.png)










![solved] Can't access data after enabling encryption - Pydio Cells - Pydio Forums solved] Can't access data after enabling encryption - Pydio Cells - Pydio Forums](https://global.discourse-cdn.com/standard11/uploads/pydio/original/2X/a/a1a431224ccc1e710ffa40927ae36ac747dc4bad.png)