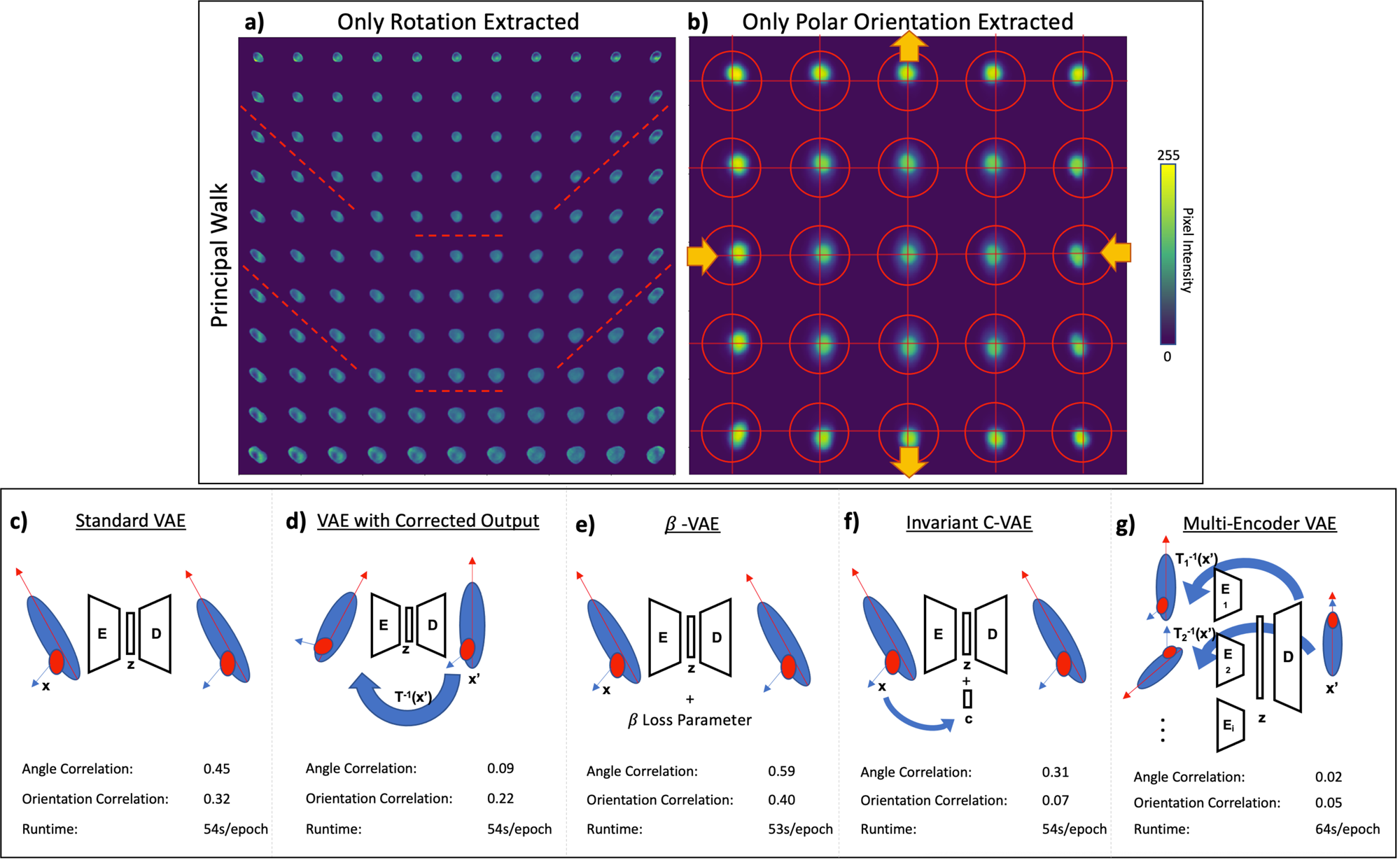
A multi-encoder variational autoencoder controls multiple transformational features in single-cell image analysis | Communications Biology

Ingestible Sensors and Sensing Systems for Minimally Invasive Diagnosis and Monitoring: The Next Frontier in Minimally Invasive Screening | ACS Sensors
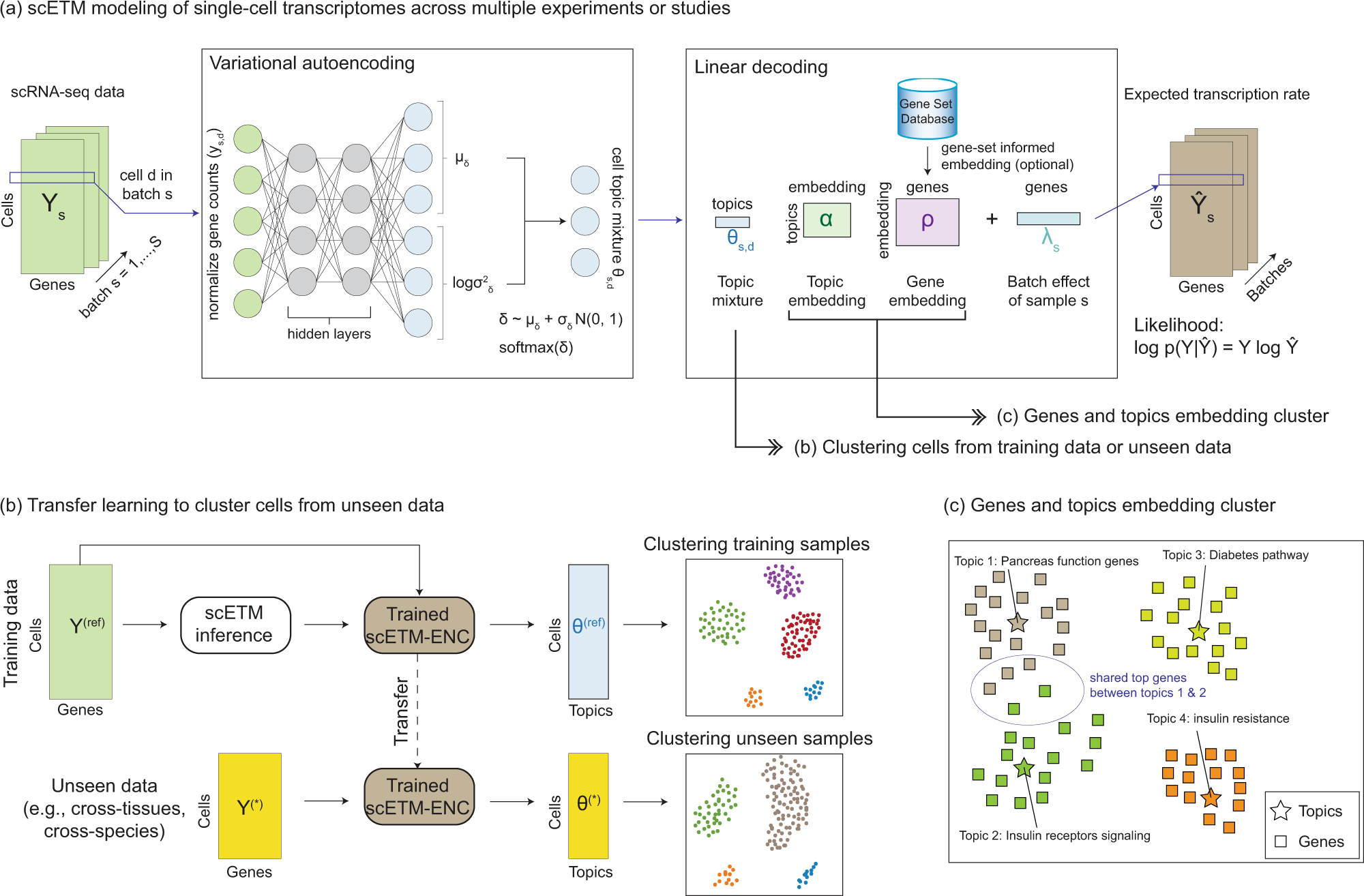
Learning interpretable cellular and gene signature embeddings from single-cell transcriptomic data | Nature Communications
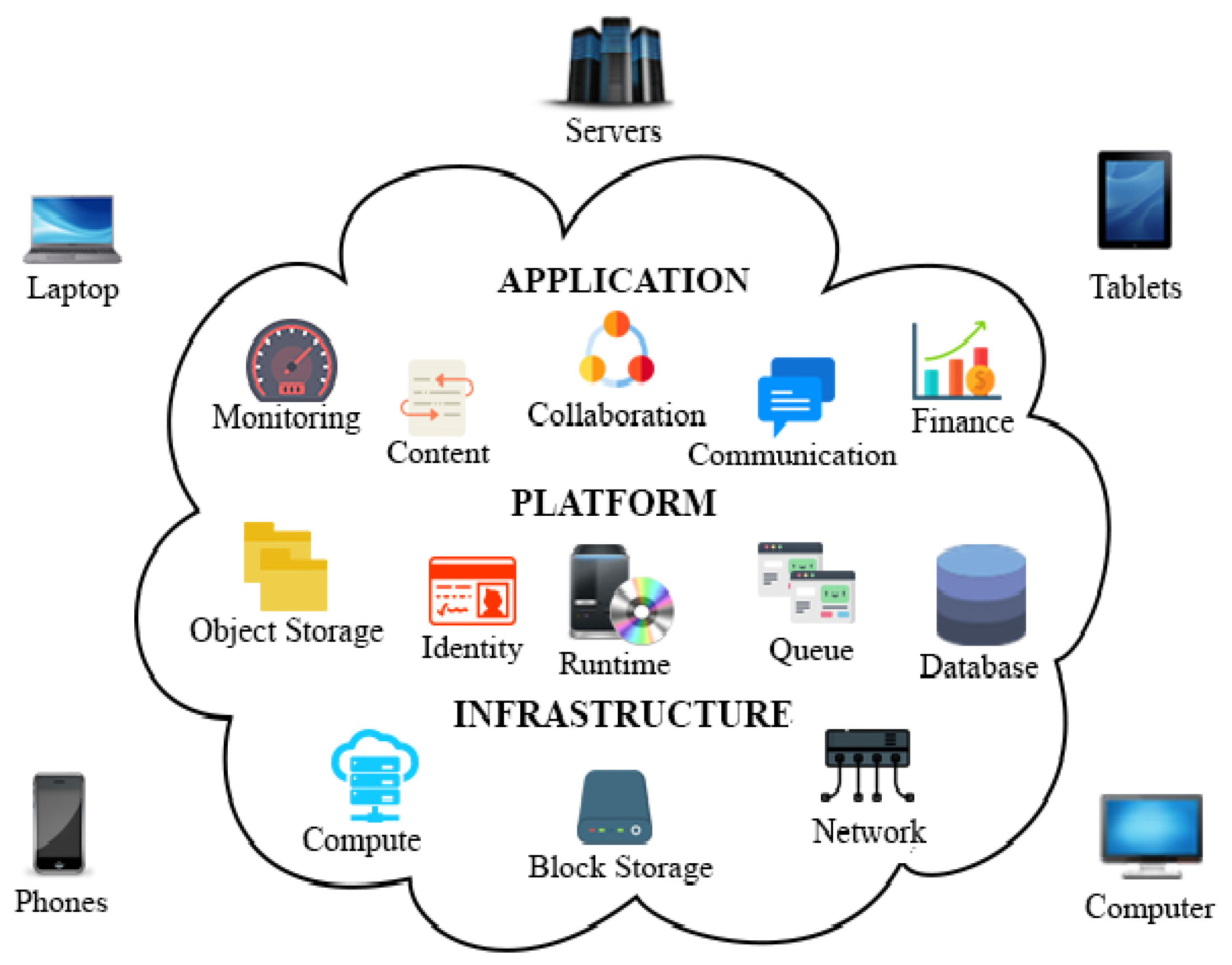
Electronics | Free Full-Text | A Survey on Modern Cloud Computing Security over Smart City Networks: Threats, Vulnerabilities, Consequences, Countermeasures, and Challenges